If an organization uses Jamf Pro to manage Mac computers, they can use Microsoft Intune compliance policies with Azure Active Directory conditional access to ensure that devices in your organization are compliant. This blogpost will explain how to setup the basic configuration if you need to integrate Jamf Pro with Microsoft Intune.
To connect Microsoft Intune with Jamf Pro we need to complete the following 3 steps:
- Create a new application in Azure AD
- Enable Intune to integrate with Jamf Pro
- Configure Conditional Access in Jamf Pro
Step 1: Create an application in Azure Active Directory
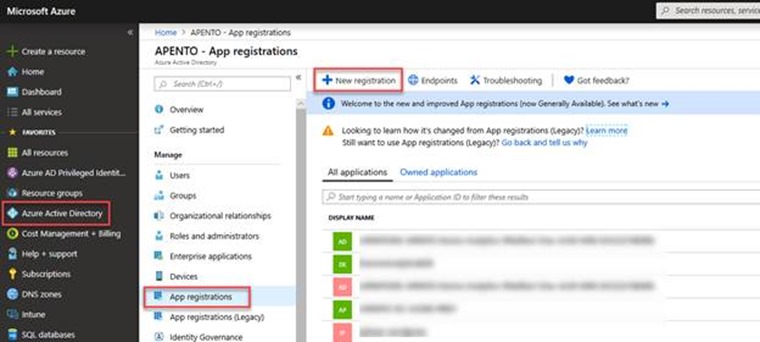
In the Azure Portal, navigate to Azure Active Directory > App Registrations, and select New registration.
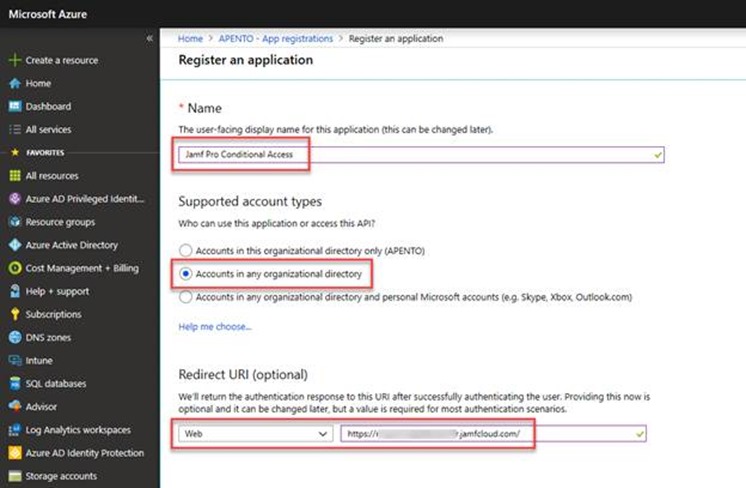
On the Register an application page, specify the following details:
- In the Name section, enter a meaningful application name (Jamf Conditional Access).
- For the Supported account types section, select Accounts in any organizational directory.
- For Redirect URI, leave the default of Web, and then specify the URL for your Jamf Pro instance.
Click Register to create the application.
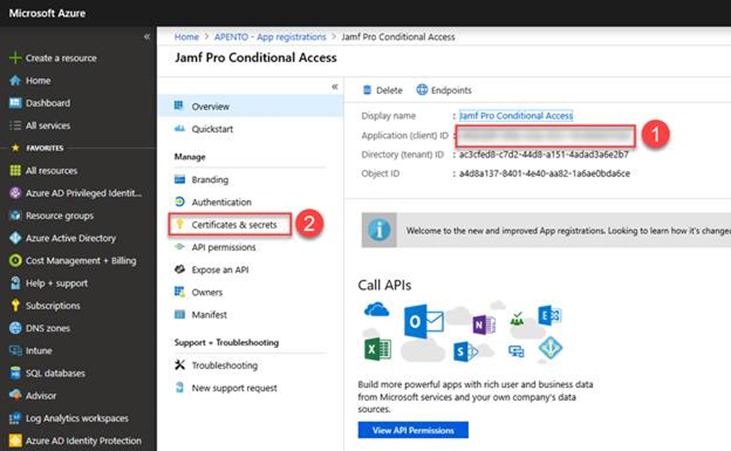
On the app Overview page, copy the Application (client) ID value and save it for later use.
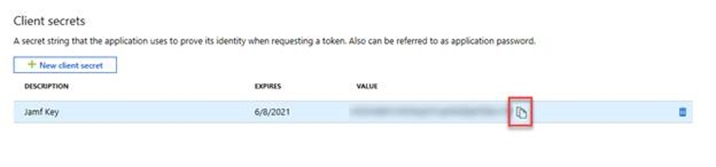
Select Certificates & secrets under Manage.
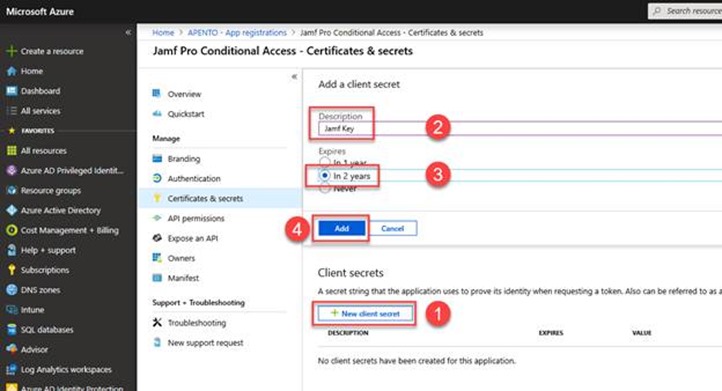
Select the New client secret button. Enter a value in Description, select any option for Expires (I normally recommend 2 years) and click Add.
Important: Before you leave this page, copy the value for the client secret and record it for later use. You will need this value in later procedures. This value isn’t available again, without recreating the app registration.
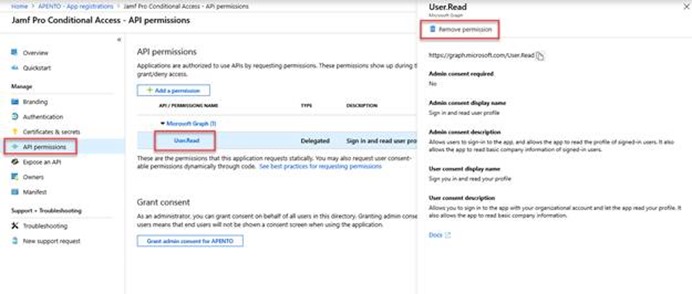
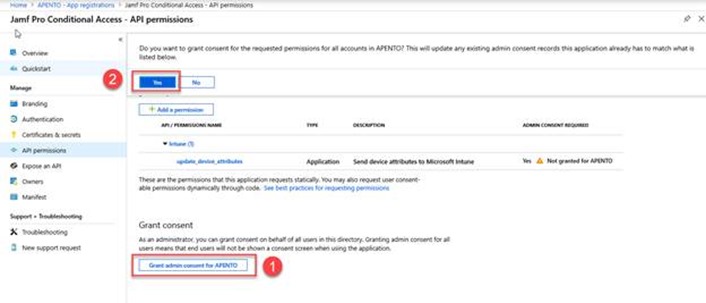
Select API permissions under Manage. Select the existing permissions and then select Remove permission to delete those permissions.
Note: Removal of all existing permissions is necessary as you’ll add a new permission, and the application only works if it has the single required permission.
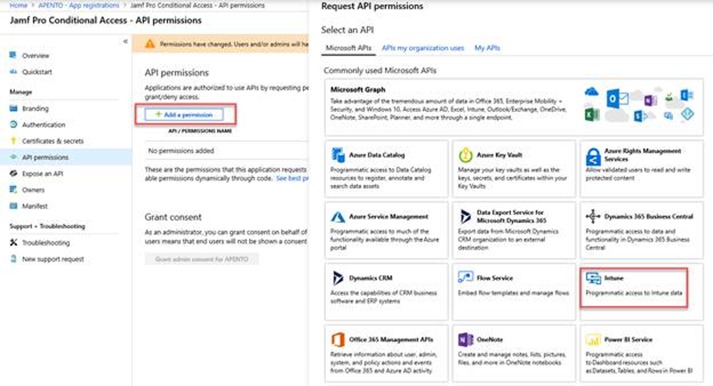
To assign a new permission, select Add a permission. On the Request API permissions page, select Intune.
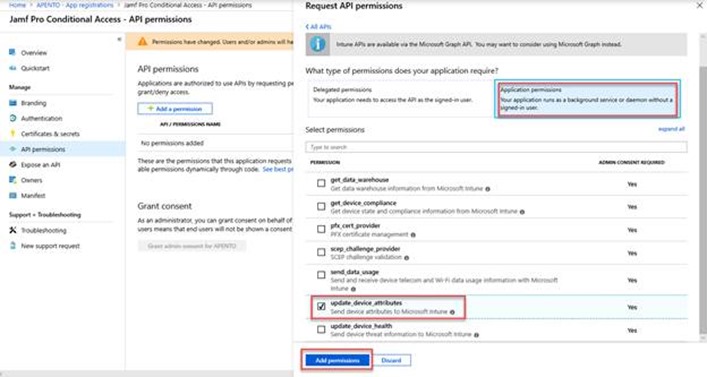
Select Application permissions and select update_device_attributes.
Select Add permission to save this configuration.
On the API permissions page, select Grant admin consent for APENTO (Org Name) and then select Yes.
The app registration process in Azure AD is complete.
Step 2: Enable Intune to integrate with Jamf Pro
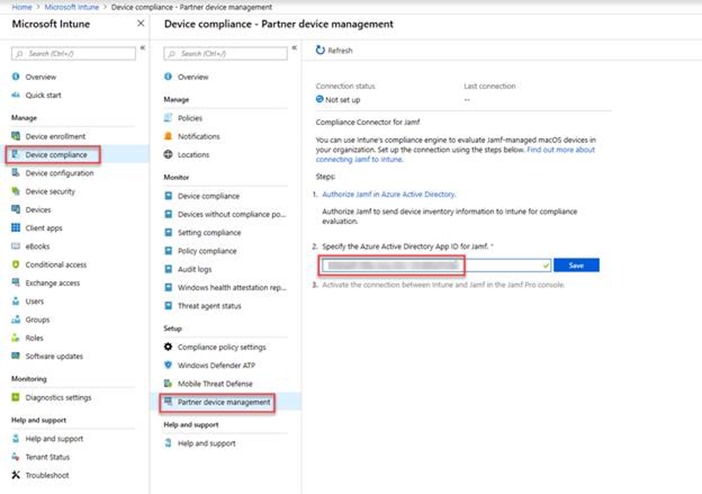
Sign in to Intune, and navigate to Microsoft Intune > Device Compliance > Partner device management.
Enable the Compliance Connector for Jamf by pasting the Application ID you saved during the previous procedure into the Jamf Azure Active Directory App ID field.
Select Save.
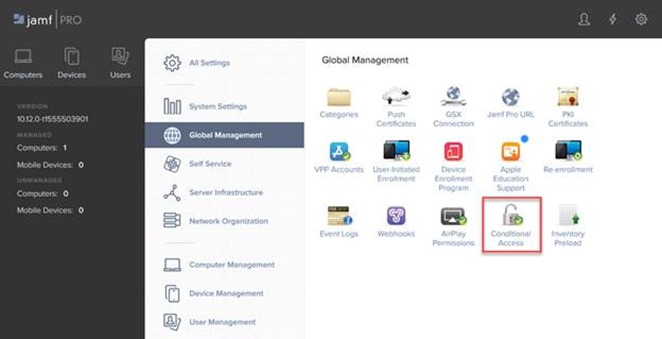
Step 3: Configure Microsoft Intune Integration in Jamf Pro
In Jamf Pro, navigate to Global Management > Conditional Access. Click Edit on the Microsoft Intune Integration tab.
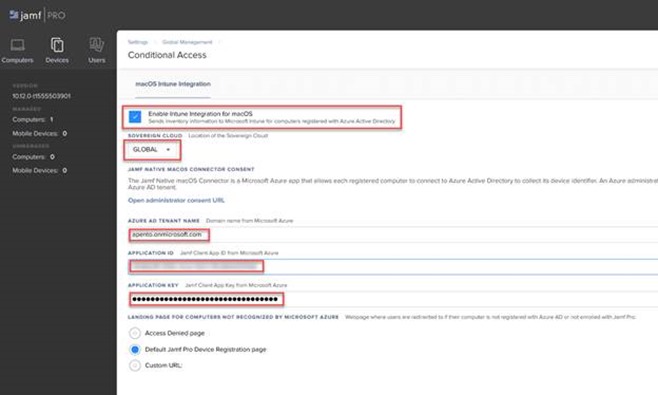
Select Enable Intune Integration for macOS.
Provide the required information about your Azure AD tenant:
- Azure AD Tenant Name
- Application ID
- Application Key (the value for the client secret that you saved earlier in this guide)
Select Save.
Click Run Test to verity your settings.
That’s it… This completes the first step of the Jamf Pro integration with Azure AD and Microsoft Intune.
/Enjoy